If you have ever experienced the acute trauma of losing your smartphone, you may be wondering if there is a way to track it when it is out of your sight. The answer is yes! If you use Apple or Android devices, you can set them up to be tracked in the event you cannot find them. Last week, we highlighted how to find Apple devices. This week, we’re shining the spotlight on Android’s Find My Device app. This app will help you find, lock, or erase Android phones, tablets, and Wear OS devices. We should probably note that your device must be running Android 8.0 or later to use all of the features of the Find My Device app.
Setting Up Find My Device
Before you can use Find My Device, there are some setup steps that need to be taken on the devices themselves. Some of these will probably already be done, like being signed into a Google account.
- Make sure your Android device is logged in with a Google account.
- Turn location on (Settings>Location>Toggle on)
- Turn on Find My Device (Settings>Security and privacy>Find My Device>Toggle on.). If Find My Device is not already installed, install it from the Google Play Store: https://play.google.com/store/apps/details?id=com.google.android.apps.adm&hl=en&pli=1
- Google states that “Store recent location” needs to be on so your device can be found if it’s offline. However, this is a relatively new feature that I have yet to find on my Pixel 5. According to their instructions, this toggle should be found in Settings>Security>Find my device.
- Make sure your device is associated with your account on Google Play, or it won’t show in Find My Device. To double-check, find your device list here: https://play.google.com/library/devices. In the upper-left of the screen, make sure the “show in menus” box is checked.
- Double-check that Find My Device works on the device by going to https://android.com/find and logging in with the same Google account as the device. You should see your device in the upper-left of the screen. If you have multiple devices associated with the account, you may need to toggle between them.
- If you want to be able to lock or erase the device remotely, you must create a 2-step verification backup code. To get backup codes, log into your Google account and select security from the left menu. Scroll down to “How you sign in to Google” and click on the “Backup codes” section. You may be prompted to enter your password again, but then you can create codes to print and use later.
Find a Lost Device
In order to use Find My Device on one of your devices, it must have power (even if turned off), be connected to Wi-Fi or a mobile data connection, and be prepared using the setup steps above to enable the Find My Device app to work. If you would prefer to watch a video on using Find My Device, there is one embedded at the end of this article. To continue with text instructions, read on!
When you log into Find My Device and select a device, notifications will be sent to the device before you select any options. If the notifications don’t help, here are your other options:
- “Play a sound” make the device ring for 5 minutes, even if it’s set to silent.
- “Secure device” will lock the device and sign out of your Google Account. You can optionally display a message or phone number on the lock screen in case someone finds (and wants to return) your device. You can still locate the device, and after finding it, you may need to log in again.
- “Erase device” is the nuclear option. It will erase all content from the device and keep it from being re-registered to a different account. You won’t be able to find it on the map after erasing it, but if it gets returned, you can reclaim it by signing in with the Google account to which it is registered.
Find Using a Browser
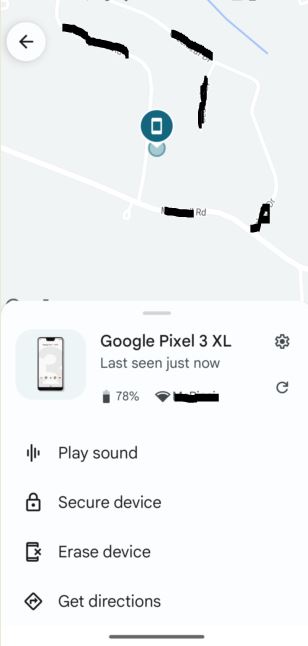
To find a device using a browser, go to https://android.com/find and sign in using the Google account your device is registered to. If you have more than one device listed on the same account, you may need to toggle between them. It will show how much battery is left and what network the device was last seen on.
Options for playing a sound, locking the device, or erasing the device are in the left menu, while a map indicating the location (or last known location) of your device is in the main part of your screen.

Find Using the Find My Device App
When using the app, you have the option of using a friend’s device that isn’t registered to your account. Whether using your own or someone else’s device to find another device:
- Open the Find My Device app on another Android phone or tablet.
- Sign in
- If your own device is lost, select “Continue as [your name]”
- If you’re helping a friend, select “sign in as guest” and let your friend sign in.
- From the listed devices, select which device to locate.
- Follow the steps from the browser above.
- You may be prompted to provide the lock screen PIN for the device you want to locate. If it does not have a PIN, you may be prompted for your Google password.
If you want to use the Wear OS watch to find a device, there are instructions here: https://support.google.com/wearos/answer/6166506?authuser=2.
Video Instructions
If you would prefer to watch a short video on using Find My Device, check this out:
Summary
Find My Device is an extremely helpful tool if you are ever unfortunate enough to need it. The flexible action options allow the user to disable the phone in the event it can’t be found, which acts as a deterrent for the resale of a stolen device. Have you ever had to use Find My Device with your Android device? If so, let us know how it went in the comments.








